ZTNA (Zero Trust Network Access) reduces the surface area prone to attack by following zero trust tenets to provide access to applications.
CloudConnexa delivers the most essential elements of Zero Trust Network Access (ZTNA). But why should that matter to you? Because we know that secure network connectivity matters to you, and you shouldn’t have to settle for a less-than-excellent solution.
We know that the complexity and cost of ensuring network security and remote access for employees and key business partners can overwhelm smaller businesses. The traditional methods of ensuring secure communications across your organization can be overly complex and expensive for a myriad of reasons:
- higher cloud adoption,
- a distributed workforce,
- mobile employees,
- the proliferation of Internet of Things (IoT) devices, and
- increasingly sophisticated cyberattacks.
The traditional methods of ensuring secure communications across your organization can be overly complex and expensive for a myriad of reasons.
Thankfully, Zero Trust Network Access reduces the surface area prone to attack by following zero trust tenets to provide access to applications.
ZTNA from CloudConnexa creates a private, secure overlay network for businesses, which connects all of their applications, private networks, workforce, and IoT devices together without needing to own and manage a multitude of complex and hard-to-scale security and zero trust VPNs. Take a look at some specific ZTNA use cases here.
Differing Definitions of Zero Trust and ZTNA Cause Confusion
ZTNA has its origins in John Kindervag’s work on zero trust model while at Forrester in 2010. According to research by ESG, there is no universal agreement as to exactly what zero trust means and how it should be implemented. While a plurality of organizations think of zero trust as a strategy, 56% continue to equate it with technology — whether segmentation-centric or identity- and access-focused.
While a plurality of organizations think of zero trust as a strategy, 56% continue to equate it with technology — whether segmentation-centric or identity- and access-focused.
Zero Trust According to Gartner
Gartner describes ZTNA this way:
“Zero trust network access (ZTNA) is a product or service that creates an identity- and context-based, logical access boundary around an application or set of applications. The applications are hidden from discovery, and access is restricted via a trust broker to a set of named entities. The broker verifies the identity, context and policy adherence of the specified participants before allowing access and prohibits lateral movement elsewhere in the network. This removes application assets from public visibility and significantly reduces the surface area for attack.”
Zero Trust According to NIST
A white paper written by the NIST on planning for a zero trust architecture states that zero trust (ZT) is the term for an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources. A zero trust architecture (ZTA) uses zero trust principles to plan industrial and enterprise infrastructure and workflows. Zero trust assumes there is no implicit trust granted to assets or user accounts based solely on their physical or network location (i.e., local area networks versus the internet) or based on asset ownership (enterprise or personally owned).
The NIST white paper points to the following key zero trust tenets as being applicable for access to resources:
- All resource authentication and authorization are dynamic and strictly enforced before access is allowed.
- All data sources and computing services are considered resources.
- All communication is secured regardless of network location.
- Access to individual enterprise resources is granted on a per-session basis.
- Access to resources is determined by dynamic policy — including the observable state of client identity, application/service, and the requesting asset — and may include other behavioral and environmental attributes.
Why Zero Trust Has an Implementation Problem
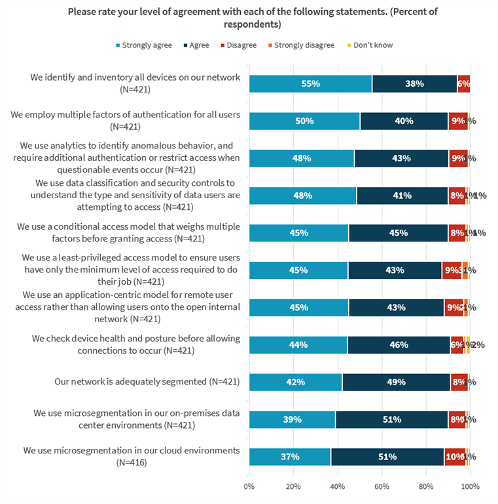
The ESG study mentioned above indicates that more than half of respondents strongly agree that their organizations identify and inventory all devices on the network and employ multiple factors of authentication for all users. However, other important aspects of zero trust, such as least privilege, conditional access, application-centric access, and analysis of device health and posture, are slightly less likely to be in place. The result is that, as far as zero trust has come in awareness and adoption, many organizations still have far to go in applying it pervasively across the enterprise.
As far as zero trust has come in awareness and adoption, many organizations still have far to go in applying it pervasively across the enterprise.
While nearly all respondents that ESG surveyed at organizations have begun to implement zero trust say they have a formalized, documented strategy that guides their cybersecurity program at least some of the time, this does not mean that such a strategy started the initiative.
Indeed, many respondents (53% and 50%, respectively) indicate that zero trust began with a specific use case and/or that a strategy was built around tools already in place in the environment. So, while critical to longer-term success with zero trust, a broad, formalized strategy is not required to begin.
While critical to longer-term success with zero trust, a broad, formalized strategy is not required to begin.
Developing a strong zero trust architecture can be a major undertaking. Consider the breadth of technologies required, the number of teams with input into strategy creation and decision making, and potential complexity as the initiative is broadened. Understandably, some organizations choose to maintain a more focused approach to zero trust.
How CloudConnexa Delivers ZTNA
CloudConnexa offers businesses a cloud-delivered service that integrates virtual networking with essential Secure Access Service Edge (SASE) capabilities such as firewall-as-a-service (FWaaS), intrusion detection and prevention system (IDS/IPS), DNS-based content filtering, and zero trust network access (ZTNA). Using our cloud VPN, businesses can easily deploy and manage a secure overlay network that connects together all of their applications, private networks, workforce, and IoT devices without owning and managing a multitude of complex and hard-to-scale security and data networking gear. OpenVPN Cloud can be accessed from more than 30 worldwide locations.
The ESG research demonstrates how ZTNA can mean different things to different policymakers. Some ZTNA policies leverage a variety of different tools to provide authentication and authorization context for these policies. As such, they can quickly become very complex.
By contrast, CloudConnexa keeps things simple and focuses on the three main aspects of ZTNA:
- Application access isolated from network access: CloudConnexa hides all applications from public view and discovery by allowing you to continue hosting applications on your private networks and avoid exposing them to the internet. All users, whether remote or on-site, need to authenticate and connect to one of the 30+ worldwide PoPs OpenVPN provides to even have the opportunity to use the applications. On connection, even authenticated users do not get access to the whole private network. In fact, our solution does not even need the IP address subnets of your connected private networks to use for routing. None of your private networks’ IP address subnet ranges are exposed as routes to the connecting devices, thus the notion of lateral movement is completely eliminated.
- Identity-based least privilege access control: All applications, not just web apps, can be configured using the domain name of the application or service. Additionally, a firewall can be applied around the application to allow only specific application protocol access. Once the applications are configured, least privilege access can be provided to them based on the identity of the user and the user’s membership to a specific Group or Role.
- Continuous authentication and authorization: Authentication takes place during every connection attempt to CloudConnexa. Zero trust access policy enforcement is continuous. Any change in the access policy is enforced in near real-time.
In addition to the above, CloudConnexa provides many features that differentiate it from other ZTNA offerings:
- Bi-directional Accessibility.
- Restricted Internet Access..
- ZTNA for IoT.
- ZTNA for Server to Server communications or API communications.
- ZTNA Between Sites.
- Automatic Network Segmentation.
- Access to Applications Hosted on Networks with Overlapping IP Address Subnets.
- Protection of Access to SaaS Apps.
- Peer-to-Peer Communications.
- Self-service Scaling.
Good to Know: CloudConnexa is a full-featured cloud-based virtual networking platform that was designed from the ground up to provide the best of virtual private network (VPN), Secure Access Service Edge (SASE), ZTNA, and SD-WAN security. Learn more about the connection between CloudConnexa and SASE here.
Not sure where to start? In these VPN Setup Examples, we provide common configurations to get you up to speed fast.
And whether or not you already use CloudConnexa, the following User Guides can help you make the most of the ZTNA CloudConnexa delivers:
- CloudConnexa Zero Trust Application Access
- CloudConnexa role-based access control to SaaS applications
- Configuring OpenVPN Access Server For Zero Trust
Below, we’ve also gathered a number of fantastic resources to help you understand the impact and value of ZTNA for your business.
Recommended Reading:
- Why VPNs and Zero Trust Network Access Are Not Mutually Exclusive — Secure remote access calls for a business VPN with a zero trust architecture in place. Learn how your business can create a layered approach to your corporate network cybersecurity strategy.
- How CloudConnexa Enables Zero Trust for Small Businesses — With CloudConnexa your small business can get a ZTNA solution without costly personnel and service providers. Even the leanest start-ups can enable secure remote access, user authentication, IDS/IPS, and monitoring.
- Embracing Zero Trust, Little by Little — Zero trust isn’t solved with one product or service. As the National Security Agency (NSA) stated in Embracing a Zero Trust Security Model, it’s a “continually maturing roadmap.”
- Why Zero Trust Access Should Be On Every CISO's Roadmap — Not creating a zero trust network is a mistake many CISOs make, and that comes at a cost — a recent survey found 97% of senior executives reported facing attempts by hackers to steal different types of credentials.
- Here’s What Happens When You DON’T Use Zero Trust Security — Humans run networks, so human error is inevitable, but this doesn’t have to result in serious damage. Holistic security procedures and protocols, including zero trust access, can make all the difference.
- Network Detection and Response Becomes More Essential as Nation State Attacks Escalate — Learn how microsegmentation down to the workload level helps organizations make their networks more resilient in the event of a breach.
Get Started Today
Ready to take your business’s secure network connectivity up a notch with ZTNA? CloudConnexa can help. Subscribe today to get started.

