Not a Flip of the Switch: How IT Managers Implement Zero Trust Models
.png)
By Krista Lyons
Over the last few years, zero trust, and more specifically zero trust network access (ZTNA) has rapidly gained popularity. In fact, according to a recent study published by ESG, the vast majority of survey respondents reported using ZTNA either extensively (46%) or for certain use cases (40%) in support of zero trust at their organizations. Only 2% cited no plans for or interest in ZTNA use.
This allure is due in part because of the overwhelming number of products saturating the market with the promise of flipping a switch and protecting your business beyond the traditional corporate perimeter.
The harsh reality? It just doesn’t work that way. No single ZTNA technology can deliver a zero trust framework. Zero trust is a comprehensive mindset that challenges the very foundations of traditional security models, one which takes time, patience, and dedication to properly implement.
In this post, we’ll dive into what implementing zero trust network access actually looks like, and how to get started.
Note: For the purposes of this post, we will be discussing ZTNA specifically, rather than the more broad concept of zero trust as a whole.
What is zero trust implementation?
Chances are, ZTNA conjures the image of either a simple solution, or an oversized, looming, stressful framework looming over your team. The truth is somewhere in the middle.
When we refer to zero trust implementation, we are discussing the process of incorporating zero trust network access principles into your existing cybersecurity policies.
According to research by ESG, there is no universal agreement as to exactly what zero trust means and how it should be implemented. However, the general consensus on the definition of zero trust is “never trust, always verify.” That means that zero trust assumes there is no implicit trust granted to assets or user accounts based solely on their physical or network location (i.e., local area networks versus the internet) or based on asset ownership (enterprise or personally owned).
Implementation of zero trust principles reduces the cost of a data breach by about $1 million, according to research from IBM. Yet, the same research found that only 41% of organizations said they have deployed a zero trust security architecture, while 59% said they haven’t.
Despite all of the debates around zero trust network access implementation, there is one thing that can be agreed on: Implementation of zero trust principles requires a combination of technology and human cooperation.
Understanding zero trust implementation
Zero trust network access relies on a few core, foundational practices. These include:
- Risk awareness – always assume an attack is underway.
- Least privileged access – limiting access to only those who need it for essential job functions.
- Multi-factor authentication and continuous verification – never trust, always verify.
Together, these core principles work to prevent bad actors from intercepting your data or getting into your network and moving laterally to access other systems. With fewer access points, you effectively shrink your attack surface. But, to recognize the full benefits you need a formalized strategy.
While nearly all respondents that ESG surveyed at organizations have begun to implement zero trust network access say they have a formalized, documented strategy that guides their cybersecurity program at least some of the time, this does not mean that such a strategy started the initiative.
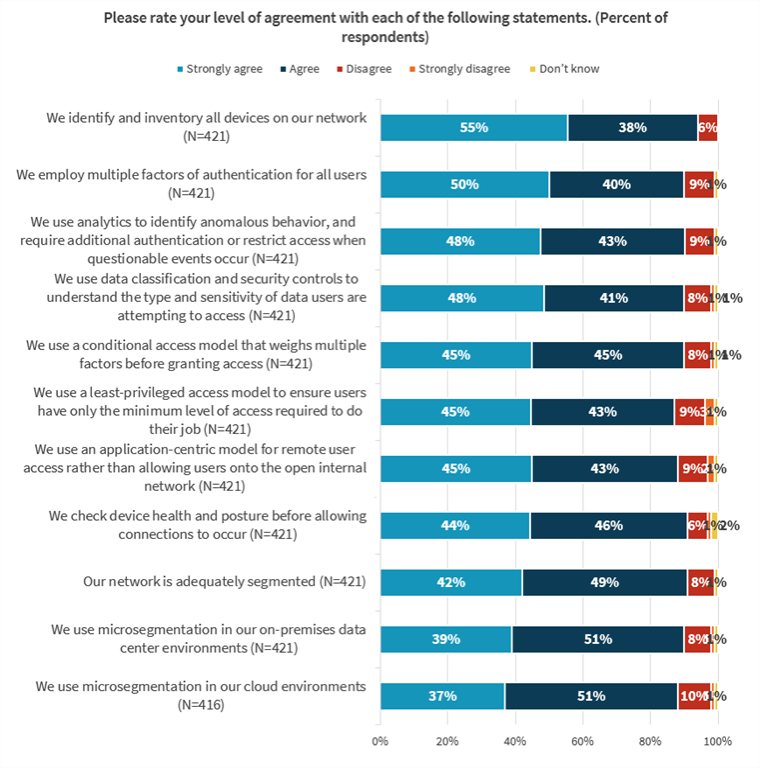
Source: ESG Research Report: The State of Zero-trust Security Strategies
What is the least privileged access in a zero trust model?
With least privileged access, no single user or account has access to all data. That means that even high-level employees, management, or executives can’t access every single asset or resource in the network. Rather, each user is assigned the permissions required to fulfill their tasks.
A few methods used to enforce least privileged access are included in the table below.
| Role Based Access Controls (RBAC) | Attribute-Based Access Control (ABAC) | Discretionary Access Control (DAC) |
| RBAC gives specific permissions to specific users or groups in order to access and manage resources necessary to their role or job function. For example, someone in a marketing function might need access to Hubspot or Wordpress, while someone in an engineering role might need access to Github or AWS. Someone in marketing would not be able to access Github, while someone in engineering would not be able to access Hubspot. | ABAC is used to set and enforce specific policies based on characteristics. Unlike RBAC, this may not be limited to your job function, but tied to other factors like the time of day, your physical location, or your manager. For example, someone who works the evening shift may require different access from someone who is working the morning shift, when financial information is being processed. | NIST defines this as “... a certain amount of access control [left] to the discretion of the object's owner, or anyone else who is authorized to control the object's access. The owner can determine who should have access rights to an object and what those rights should be.” For example, someone who uses Google Docs and shares access to the documents needed for a project with only those they deem necessary is using DAC. |
What is multi-factor authentication in a zero trust model?
As we mentioned earlier, the main idea of zero trust is “never trust, always verify.” Multi-factor authentication (MFA) is one of the simpler ways to implement that. In fact, you likely have already implemented MFA for individual apps and systems.
As noted by the Cybersecurity and Infrastructure Security Agency (CISA), “Implementing MFA makes it more difficult for a threat actor to gain access to business premises and information systems, such as remote access technology, email, and billing systems, even if passwords or PINs are compromised through phishing attacks or other means.”
MFA requires users to present two different credentials when logging in to an account. For example a 6 digit code generated using an authenticator app in addition to their password.
How security teams drive zero trust implementation within organizations
Security teams are the starting point for zero trust implementation because they can implement MFA and access groups. However, when it comes to implementing zero trust, the security team or IT manager’s role doesn’t stop there.
The rest requires a cultural shift and a change in the traditional ways of thinking about security. And, it requires teammates to commit to using the systems in place and avoiding shadow IT.
How to implement zero trust network access
Now that we know more about the zero trust model, let’s answer your burning question: how to implement zero trust.
Define the attack surface
It has been said that you should always know your enemy, but in reality, you should start by knowing yourself… or in this case, your company’s attack surface and weak points.
Start by defining the current network infrastructure to identify security gaps. You’ll need to assess the following four areas that are often most vulnerable to attack:
- Sensitive data/proprietary information
- Critical applications, including SaaS apps
- Physical assets (PoS Terminals to IoT devices)
- Corporate services (day-to-day infrastructure that everyone in the organization uses)
While you assess these areas, get into the mindset of an attacker. Where will they be most likely to launch an attack – whether simple or complex? What is the most likely method of attack? Which social engineering tactics would be most likely to compromise your business? All of this will help you understand which segments of data and access need to be segmented and blocked.
Establish trust boundaries and segment network access
Once you’ve assessed your attack surface, you can begin considering your trust boundaries and network access segmentation. For example, you may want to establish that VLAN A should not talk to VLAN B. Or that IOT VLAN should not communicate with specific users or servers.
You will also need to consider user groups and access levels for each group – essentially creating boundaries around each team so that there is less of an opportunity for a bad actor to get in through, for example, a marketing employee’s credentials and then quickly move into the accounting applications and software to steal financial data.
Going a step further, you can set up application access that is isolated from network access, by setting up access control for users.
Configure a zero trust network
Configuring your zero trust network sounds more complicated than it actually is. The first step in configuring your zero trust network is setting up secure remote access for anyone and everyone who will connect to your network.
You’ll also need to implement multi-factor authentication for enhanced security. Additionally, you can use company-wide verification or SSO process, including:
- Local Authentication
You can use local authentication and password hashes (SHA256) stored in the user properties database to verify credentials during login. - PAM Authentication
Manage PAM authentication on your server, using local user accounts in the operating system where Access Server is installed, or on a separate but reachable server. - LDAP Authentication
UseLDAP authentication services to provide more secure authentication for your users and one source of truth for user management. - RADIUS Authentication
Enable RADIUS authentication (PAP, CHAP, and MS-CHAP v2 supported), accounting reports, and case-sensitive matching. - SAML Authentication
When you enable SAML authentication, users get a single sign-on (SSO) experience that uses IdP credentials. - Custom Authentication
You can write custom Python3 code, using post_auth scripts, to load into the post_auth programming hook as a supplemental or replacement authentication system. - Simultaneous Auth Systems
You can also use multiple authentication systems simultaneously, so you can define one default system and optionally configure other systems by group or user. - TOTP Multi-factor Authentication
Add another layer of security with multi-factor authentication (MFA) using time-based one-time passwords (TOTP), an industry-standard way to store a secret key on a user device. - Certificates and Private Keys
On top of user-credential authentication, you can use private keys and public certificates to verify client and server identity.
All users, whether remote or on-site, will need to authenticate and connect to the company VPN to use applications or even see login screens. To make it more secure, you can configure access control so that authenticated users get least privilege access.
Create a zero trust policy
We have said it before and we will say it again (and again, and again) because it bears repeating: zero trust is not a single product or a flip of a switch. So while you may have configured your network to comply with zero trust principles, it takes creating a zero trust policy to fully realize the benefits of zero trust.
Zero trust security policies should be granular and applied across the entire organization. These policies should be adaptive, so user access privileges are continually reassessed as context changes.
Zero trust policies define access control, the security posture of each device (including IoT devices), and which groups or users can access which parts of the network. Zero trust policies also help you ensure that least privilege (giving access to only the necessary apps and systems and no more) always applies.
In other words, your zero trust policy should attempt to answer the following questions:
- Who: Who is attempting to gain access?
- What: What is the user attempting to access?
- When: When is this access request occurring?
- Where: Where is the resource located, and where is the user located? Are they located in an authorized place from an authorized device?
- Why: Why is the user attempting to access this data? Do they need this for their job function?
- How: How can access be efficiently and effectively provided without putting the network and business at risk?
Here are two examples of zero trust policies in OpenVPN’s products:
- Identity-based least privilege access control: All applications, not just web apps, can be configured using the domain name of the application or service. Additionally, a firewall can be applied around the application to allow only specific application protocol access. Once the applications are configured, least privilege access can be provided to them based on the identity of the user and the user’s membership to a specific Group or Role.
- Continuous authentication and authorization: Authentication can take place during every connection attempt. Zero trust access policy enforcement is continuous. Any change in the access policy is enforced in near real-time.
- Device Identity Verification & Enforcement (DIVE): ZTNA is not just for remote workers. Your on-prem workers need to be safeguarded as well. CloudConnexa's DIVE is a new approach to enforcing one of the key principles of ZTNA: least Privilege, by allowing Owners and Administrators to restrict application access to only authorized devices. This is accomplished by establishing a 1:1 relationship with a user’s connection Profile and the device’s UUID and allowing only authorized device IDs to connect.
Monitor and improve your network
You’ve got your zero trust network and policies set up, you know your attack surface and your network segmentation is in a good spot, so you’re done, right?
Not quite.
You must continually monitor your network – but if you’re an SMB you likely will need to do this with automation to keep from adding more to your team’s plate. You can do this in a few ways, for example:
- Automated log streaming through your VPN provider to see tunnel connections, disconnections, and failed connection attempts, allowed and blocked traffic flows, blocked access due to content filtering policies, and blocked access due to intrusion protection policies.
- Setting weekly, monthly, or quarterly reminders to check permissions for employees and review any employee credentials that may have changed due to promotion, department changes, or termination.
- Periodically reviewing and ensuring that MFA methods are still being used and implemented across all departments.
Key considerations in zero trust implementation
Zero trust sounds simple in theory, but there are a few potential roadblocks and challenges to be aware of.
The importance of continuous updating to zero trust policies
Zero trust is not effective if your team constantly changes, employees are terminated, or access levels are not kept up to date. You must continually review, update, and refresh your zero trust policies. The frequency is up to you, but we recommend at least quarterly reviews of your zero trust policies, groups and user access, and log streams to identify potential weak spots or attempted attacks.
The role of zero trust in protecting sensitive information
Zero trust can often be seen as restricting your employees, but in reality it is about protecting sensitive information, especially while it’s in transit. Zero trust requires encryption. The Advanced Encryption Standard (AES) is the standard encryption algorithm used by the U.S. Government and countless organizations. TLS for email, HTTPS and SSL for websites, and the use of a VPN when connecting from public Wi-Fi hotspots (even those that say they are secure) are some ways that organizations utilize encryption to secure their most sensitive data.
Implement multi-factor authentication for enhanced security
As we mentioned earlier in the post, MFA will enhance your security level and ensure that you are truly adhering to the principles of zero trust network access.
Tips for effectively communicating zero trust network access implementation
Communication is key. Getting employee buy-in for ZTNA takes a shift in mindset. To effectively communicate the shift to zero trust, it’s important to share the motive behind the change with your team. Communicate in both writing and a town hall style meeting that the change does not mean you don’t trust your team members, but that you simply must all verify continually.
Challenges of zero trust implementation (complexity, cost considerations, user adoption)
Among the main challenges in implementing zero trust are the (perceived) complexity or complex infrastructure, cost of network security tools, and simply getting users to adopt the practice. Many of these hurdles can be overcome with clear communication. For example, communication between your IT team and change managers as well as your employees can reduce the complexity and user adoption challenges. And often the tools you already use – such as corporate VPN tools – can reduce the added costs. The key here is to plan and discuss potential challenges and try to map out your plans to address them.
Embracing the zero trust journey
Zero trust can help secure your network and add an extra layer in your cybersecurity plans. But, it takes a proactive approach to see the full benefits. Zero trust is not a switch to flip, but implementation doesn’t have to be overly complex.
OpenVPN can help your organization with the most important tenets of zero trust. To find out how we can help, download and try CloudConnexa or Access Server for free. You can also check out our interactive product demo here, or watch our recent webinar all about zero trust in healthcare with OpenVPN.


.png)